Cybersecurity is any technology that protects internet-connected systems, networks, and programs from cyberattacks. Cybersecurity protects sensitive data, devices, software, and hardware from cyber attacks such as ransomware, phishing, and DoS attacks.
Importance of Cybersecurity
Prevention of data leaks– Our society has become more technological. Sensitive information like credit card information, identity proof, and bank account details are all stored in Google Drive or Dropbox. To prevent sensitive data leaks, we need Cybersecurity.
Protection of devices– The main entry points of cyber-attacks are desktops, laptops, and mobiles. Cybersecurity protects these devices and their users from attacks. The protection of devices is essential for an organization or business.
Security applications– Cyber Security protects applications from unauthorized access and data breaches. It ensures that authorized users have secure access to the network, and at the same time, it prevents unauthorized access. It is crucial to maintain the loyalty of e-commerce businesses.
Mobile security– Mobile security is significant for our modern society. Everyone has private messages, photos, and videos on their desktops, laptops, or smartphones. Mobile application management is one of the best technologies to provide mobile security.
Preserving national security– Cybersecurity is crucial for the nation also. Cybersecurity prevents all cyber-attacks on government systems and military networks. Governments also prioritize Cybersecurity to protect assets against digital threats.
Cyberattacks are increasing day by day.
Cyberattacks steal a system or person’s information by hacking networks or devices. Hackers can control anyone’s system and breach information, which causes financial losses.
Phishing attack– Attackers send you an email or malware links after you click the links, software containing malware or viruses that steal data or information from the system and send it to attackers. This type of attack is called a phishing attack. When attackers target C-suite profiles like co-founders, the vice-president called whale phishing. When the attackers focus on a specific organization to steal information, it is called a spear phishing attack.
Attackers can attack through scam emails, fake websites, and malware, so we should analyze links to click before. In the year 2014, it was found that cyber attackers, through the phishing attack, got all the information and details from LinkedIn, targeted them with an email phishing attack, and stole 100 terabytes of data and a massive data leak from Sony.
Password attack – We use passwords to protect our sensitive information. Using the hit-and-trial method, attackers can easily steal the password. They use different combinations using your name, birthplace, date of birth, etc. Attackers steal your private videos, photos, information and blackmail you for not sharing publicly. In May 2019, a hacker named GnosticPlayers attacked CANVA and took away the data of 139 million users. GnosticPlayers is using the brute force method and getting passwords to an admin account, which leads to a massive data leak.
DoS attack– Denial of service or an attack where attackers send massive traffic to overload systems. Attackers inundate a server with redundant requests which causes a slow performance, disrupting service to intended users. DoS attack attacked Amazon Web Service, the biggest company in cloud computing, in February 2020. The attackers amplify the data sent to the victim’s IP address 56 to 70 times. This attack lasted for three days.
Malware – Malware is malicious software. Attackers trick you with scam emails and fake links to install the malware. If a person installs the software, he never recognizes the malware. However, the malware steals the data and damages his devices. The newest threat is Clop ransomware (CryptoLocker, Locky, WannaCry). CrypttoLocker was released in 2013 and caused 3 million USD in damage. WannaCry was introduced in 2017 via phishing emails and caused more than 4 billion USD in damage. Eavesdropping attack- Attackers secretly intercept communication between clients or servers. It is also known as the Man in the Middle attack. Attackers mainly swap their IP addresses with users. Hackers can access confidential information and databases.
Prevention methods of cyberattacks
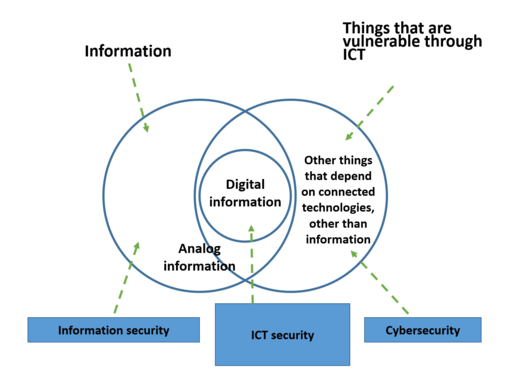
With the ever growing threats in the business as well as in the corporate networks in order to maintain cybersecurity is becoming a very crucial aspect. To ignore every kind of threat within their administrative operation the business needs to follow several prevention methods to safeguard their business effectively and to ignore those risks.
Security awareness training – Security awareness training is crucial because attackers access sensitive information through employees. They need to check links to click before checking the email address from the received email.
Updates system – Cyber Attacks happen because systems or software are not updated. The less updated system has many weaknesses, and hackers exploit these weaknesses to gain access to data. Endpoint protection protects all the devices connected through a network.
Install a firewall – The most effective way to prevent cyberattacks is to put the network behind a firewall. A firewall can block threats and malicious traffic from the network. A firewall arrangement will block any brute force attacks made on your network before it can do any destruction, something we can assist with.
Antivirus – Antivirus is essential for a computer because it can scan the entire system for malware.
In the era where AI is growing rapidly, it is important for all to take care and understand the aspect of cyberattacks and cybersecurity as a whole.


